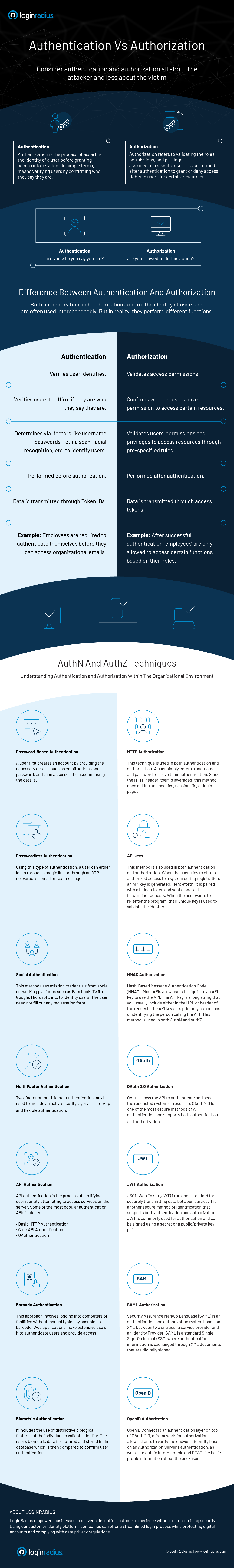
In this article, we will be going over two concepts people tend to confuse in the world of identity and access management. Simply put, authentication validates that users are who they say they are, while authorization permits those users to access a resource.
What is Authentication?
Authentication is the process of validating that users are who they claim to be. Passwords are one of the most common ways to authenticate a user on a system. If the username matches the password provided by the user, it means the identity is valid, and the system proceeds to grant access to the user.
Other ways of authenticating users include:
- One-time pins (OTP) - These grant access for only one session or transaction.
- Authentication apps - They generate security codes via an outside party that grants access.
- Biometrics - Here, a user presents a fingerprint or eye scan to gain access to the system.
Some systems might require the successful verification of more than one authentication factor before granting a user access. This is called two-factor authentication (2FA) or multi-factor authentication (MFA) and is often used to increase security beyond what passwords alone can provide.
What is Authorization?
Authorization is the process of giving a user permission to access a specific resource or function in a system. This term is often used interchangeably with access control or client privilege.
Popular authorization techniques include:
- Role-based access controls (RBAC) - They can be implemented for system-to-system and user-to-system privilege management.
- JSON web token (JWT) - This is an open standard for securely transmitting data between parties, and users are authorized using a public/private key pair.
- SAML - This is a standard Single Sign-On format (SSO). Here, authentication information is exchanged through XML documents that are digitally signed.
- OpenID authorization - This verifies user identity based on an authorization server’s authentication.
- OAuth - This allows an API to authenticate and access a requested system or resource.
Moving Further
To learn more about authentication and authorization concepts, differences, and techniques, check out this infographic created by LoginRadius.
Authentication and Authorization with Auth0
Auth0 is a flexible, drop-in solution to add authentication and authorization services to your applications. It allows your team and organization to avoid the cost, time, and risk that comes with building a custom solution to authenticate and authorize users. You can read more about Auth0 here https://auth0.com/docs/get-started
